[vc_row][vc_column][vc_column_text] What’s an email bomb? In the world of computers and networks, a “mail bomb” or “email bomb” is a system that floods a particular email inbox or email server with messages – enough to possibly overload the system and cause it to stop working properly. How does an email bomb work? Multiple ways of […]
Category Archives: Blog
[vc_row][vc_column][vc_column_text] What is Identity theft monitoring? Identity theft monitoring is when a company keeps an eye on your identity and will notify you of those who are trying to steal it. This could prevent years of credit issues or the loss of your money. Have you suffered at the hands of identity theft? If not, consider yourself […]
[vc_row][vc_column][vc_column_text] What is Check Kiting? Check kiting is a popular form of fraud that allows a person to take advantage of non-existent money in a bank account by using bad or “hot” checks as a form of unauthorized credit. How does it work? Kiting can leave a large amount of damage to a financial institution, […]
Why are children more likely to suffer identity theft? We all know that tens of millions of adult files and records are routinely stolen and used to enable identity theft around the globe. But one of the lesser known problems associated with identity theft is that children are now the newest victims of fraud, and […]
[vc_row][vc_column][vc_column_text] What is SSL and TLS Encryption? While using your web browser, you might notice the web address of some websites appearing as “https,” rather than the usual “http.” You might also notice a small lock or padlock icon in the status bar of the web browser. That signals a form of SSL or TSL […]
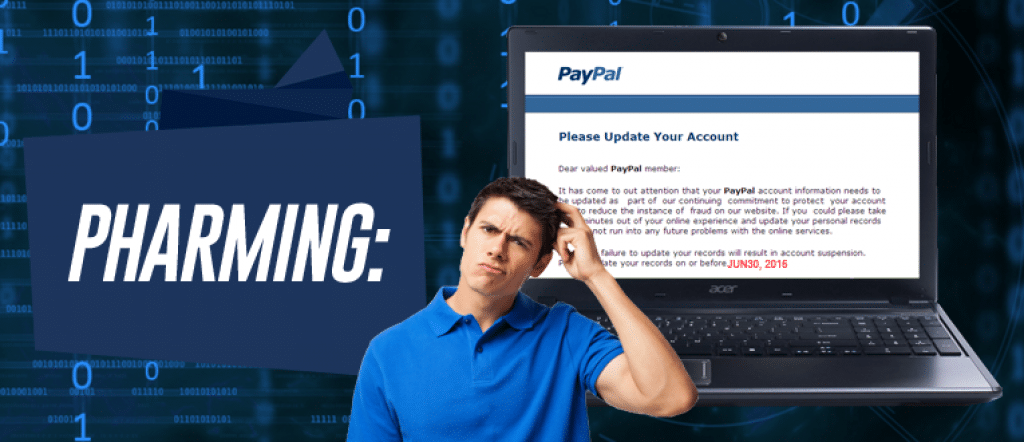
[vc_row][vc_column][vc_column_text] What is Pharming? In the cyber world, Pharming is a fraudulent method identity thieves use to redirect a user to a bogus website in order to get personal information. Victims won’t even necessarily know what has happened. How pharming works Pharming occurs through Domain Name System (DNS) “poisoning.” In this type of attack, a domain […]
[vc_row][vc_column][vc_column_text] What is Scareware? The threat of your computer being infected with “scareware” is no Halloween joke. Scareware is a dangerous computer program that tricks or scares a user into paying for a useless product or downloading a malicious program such as malware. Scareware has been called many other names including fraudware, deception software, and […]
[vc_row][vc_column][vc_column_text] What is Ransomware? Like the name implies, “ransomware” is essentially a malicious program that allows your computer or server to be sabotaged and held at ransom, while cybercriminals demand you do something for them in order for you to regain access. Often, hackers demand money under the threat that they will erase everything you’ve […]
What’s a Honeypot? Honeypots are a form of web security used to detect, deflect, or gather information about unauthorized use. Keeping your computer systems safe may require the use of deception, and a honeypot may be just the key. How do they work? In a sense, a honeypot is a decoy, sort of like a […]
[vc_row][vc_column][vc_column_text] What is a Hacker? If your identity has been stolen online or if you hear stories in the news about others who have been victimized by cybercriminals, there’s a good chance you’ve seen or heard the word “hacker.” But do you know what or who a hacker really is? A hacker is anyone who […]