How Many IoT (Internet of Things) Gadgets do you have? A tidal wave of Internet-connected devices is poised to hit the consumer market in the next year as every technology product imaginable – from toasters to tennis racquets – will be WiFi enabled. But while this may be greeted with enthusiasm by many consumers, security […]
Category Archives: Blog
[vc_row][vc_column][vc_column_text] What is jailbreaking? Jailbreaking is the removal of restrictions that are set on various devices, such as those on an electronic tablet or smartphone. Jailbreaking a device allows a user to unlock and install applications and make other changes not necessarily approved by the manufacturer of the software. How does it work? Because jailbreaking […]
[vc_row][vc_column][vc_column_text] What is a Grey hat hacker? In the computer world, there seems to be a group of skilled technicians who toe the line between good and bad: the grey hat hackers. Although the word hacker is commonly thought to refer to a skilled computer genius who uses his or her talent to harm others with […]
[vc_row][vc_column][vc_column_text] What is a white hat hacker? Hackers are often divided into three metaphorical categories: white hat, grey hat, or black hat. These names, according to Norton, have their origins in spaghetti westerns, which often featured a “good guy” who wore white hats, and a “bad guy” who wore black hats. When it comes to […]
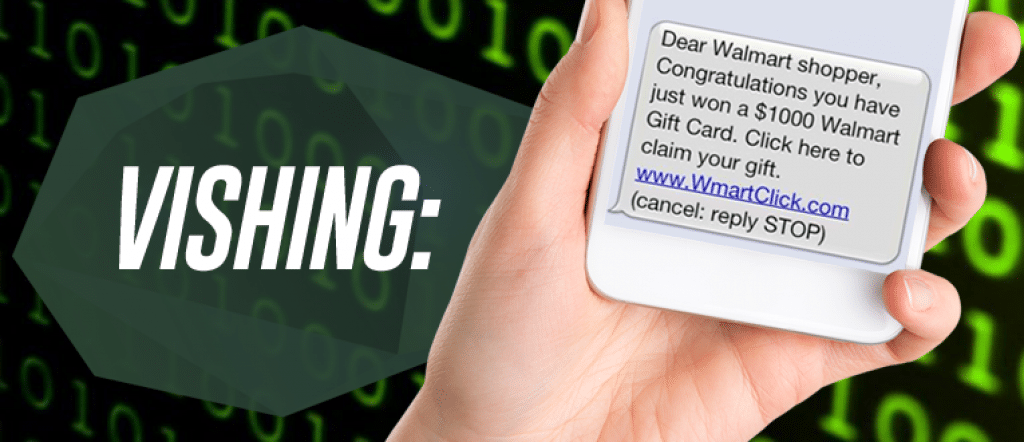
[vc_row][vc_column][vc_column_text] What is Vishing? Though you may have never heard of the term vishing, there’s a good chance you’ve been targeted by this very criminal activity. Vishing attacks rely on a phone network to steal your money and other personal information. The word “vishing” is a combination of “voice” and “phishing,” the online scam aimed […]
[vc_row][vc_column][vc_column_text] What is Koobface? Back in 2008, messages sent through popular social media programs and through major email websites became infected with malware that came to be known as the Koobface virus. Koobface is a virus used to target Windows, Mac and Linux operating platforms intended to infect your computer with malware. How does Koobface […]
[vc_row][vc_column][vc_column_text] What is SEO Poisoning? Search poisoning, or SEO poisoning, is the use of search engine optimization tactics to make a dangerous website appear legitimate and prominent in results of an online search. What is SEO and how does SEO poisoning work? Search Engine Optimization is a method of using certain keywords or other signals that […]
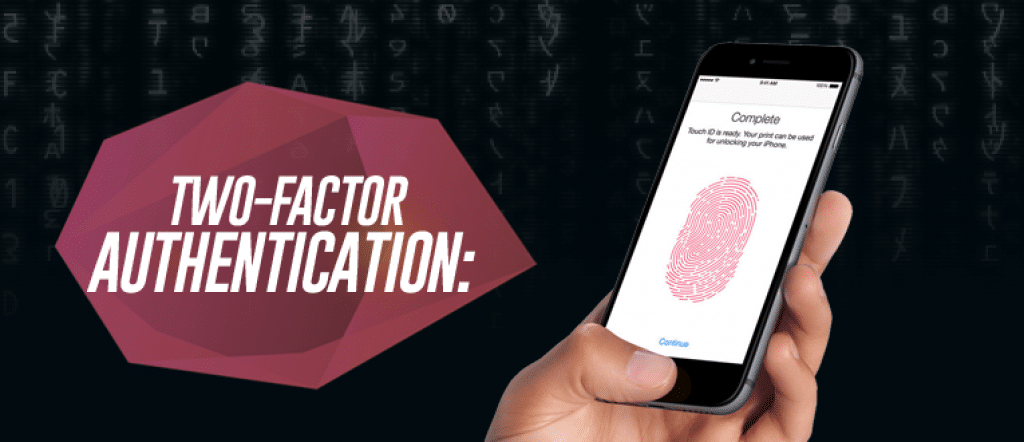
[vc_row][vc_column][vc_column_text] What is two-factor authentication? Also known as “2FA” or “TFA,” two-factor authentication is considered an added layer of protection that requires a username and password, along with a second method of verifying your identity, such as a fingerprint, retina scan, bank card or even a smartphone application. How does two-factor authentication work? Simply relying […]
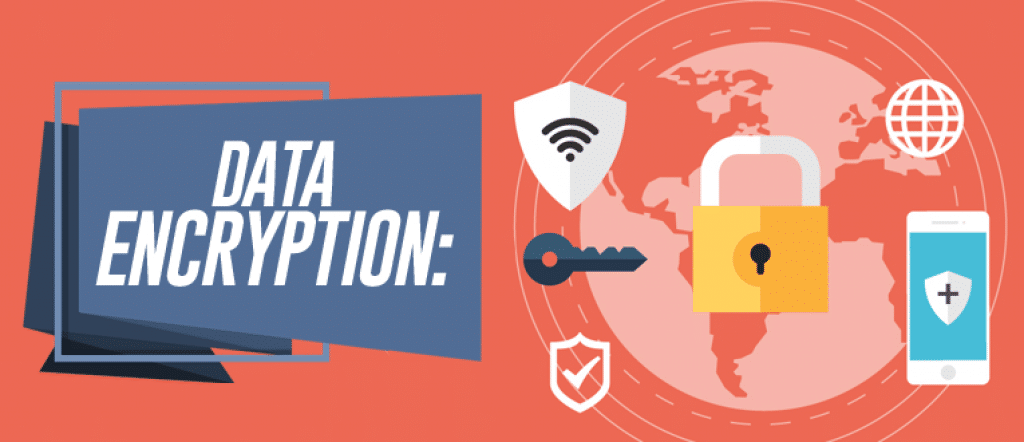
[vc_row][vc_column][vc_column_text] What is data encryption? The encryption of data is a method of altering electronic information into a form that allows only authorized users to read or understand what is being sent. In theory, data encryption prevents anyone who sees the information from being able to understand it and use it for criminal purposes such […]
[vc_row][vc_column][vc_column_text] What is a keylogger? Keystroke logger – also known as a “keylogger” – is when every keystroke you make on your computer is tracked and recorded, usually without your authorization or knowledge that it’s happening. The dangers of keyloggers Criminals bent on stealing your identity can do so easily when they know everything you’ve […]