Dealing with
Identity Theft
The
Definitive
Guide

A Step-by-Step Guide for
Responding to and Protecting
against Identity Theft
This step-by-step guide will help you to regain control of your financial life at a time when people feel helpless and are uncertain what to do. We will go over every aspect of identity theft, including websites to visit, organizations to contact, forms to fill out, samples of the kinds of letters to send, prevention, and more.
If you ever become a victim of identity theft, it’s imperative that you take quick action to protect yourself from any further damage to your credit and to fix the situation quickly.
Table of Contents
So if you think that you may be a victim of identity theft, don’t delay, and get started by following these step-by-step instructions:
Contact any business where you know or
suspect that fraud occurred.
Call the management, or the fraud department if there is one, and explain
your situation. Ask to close or freeze your account. If you have been using
the company’s website, immediately change all of your online passwords.

Contact all three credit bureaus and place a fraud alert
A fraud alert makes it harder for an identity thief to open new accounts in
your name.Once an alert is placed, businesses must verify your identity
before they can issue credit. The alert is free and lasts for 90 days, at
which point it can be renewed. By law, any of these bureaus that you
contact must also inform the other two on your behalf, but call all three
just to be on the safe side.
Order your credit reports through these bureaus. You’re entitled to receive one free credit report per
year, which can be obtained through www.annualcreditreport.com.
Depending on the current volume of requests, the reports are typically mailed out within 15 days. If a
delay occurs, the credit bureaus will let you know the approximate timetable.
Review your reports and make note of anything
that you don’t recognize.
This step will help when reporting facts to the police and to the Federal
Trade Commission (FTC), the government agency that helps victims of
identity theft. Also be sure to check that all of your information, including
your name, address, social security number, and prior employers, is free
of errors.

Complete the online form available from identitytheft.
gov, or call 877-438-4338.
It is important to create an account with identitytheft.gov because this
agency will work with you on your Identity Theft Affidavit and recovery
plan.
File a police report.
Tell the police that your identity has been stolen
and that you need to file a report. Make sure
that you receive a copy of the police report.
The combination of the Identity Theft Affidavit
and police report amounts to an identity theft
report.
If, however, you are unable as a victim to
obtain an identity theft report from the
police, here are a few options to consider:
- Check to make sure that the law in your state
does in fact require the police to create
reports for identity theft victims. - Present a copy of the FTC Memorandum to
police on the importance of police reports
in combatting identity theft. - Go to a different police station or a different
law enforcement agency, such as the state
police, if your local department isn’t helpful.
Go to the nearest police station, and make
sure to bring these items with you:
- a copy of your FTC Identity Theft Affidavit
- a government-issued ID with a photo
- proof of your address (examples: utility bill, rental agreement)
- any evidence of the theft (examples:
unauthorized bills, bank statements)
An identity theft report is a police report that
includes specific information for credit bureaus
and/or creditors that can help to determine
the validity of identity theft claims.
The police are sometimes hesitant to help
victims of identity theft on the grounds that
they are too busy or have to give higher priority
to other kinds of crimes. Be insistent: most states
require the police to write and file reports for
identity theft crimes.

Once you have completed the steps
outlined above, it’s time to repair the
damage and protect your identity
for the future.

The following steps are crucial to reestablishing your credit.
Close any new accounts that have been opened in your name and remove any
fraudulent charges from your accounts
- Contact the fraud department of each business, as discussed above.
- Explain your situation.
- Inform each business regarding which charges are fraudulent and ask to have them removed.
- Tell the affected businesses to close your accounts and create new ones.
- Request that each business send you a letter confirming that they are remov-
ing all of the fraudulent charges and that you are not liable for any of them. - Keep a record of every conversation you have about your situation that
includes the person with whom you spoke, the time, and the date. - Keep these all of these documents in case something negatively impacts
your credit rating.
Some businesses may require you to send them a dispute form. The FTC
provides sample letters to get you started.
Fix your credit report for each
credit bureau.
Write to all three credit bureaus
using this sample letter.
- Include a copy of your Identity Theft Report and proof of your identity..
- Point out which items on your report are related to the identity theft.
- Ask each bureau to block the in-correct information.
- Send the letters to each credit bureau from your local post office by certified mail and be sure to hold on to the return receipt.
Here is contact information for each of the three bureaus and where to send your letters:
TransUnion.com
phone: 800-680-7289
Fraud Victim
Assistance Department
P.O. Box 2000
Chester, PA 19022-2000
Equifax.com
phone: 800-525-6285
P.O Box 105069
Atlanta, GA 30348-5069
Experian.com
phone: 888-397-3742
P.O. Box 9554
Allen, TX 7501
After you have followed all of the steps outlined above and are on the road to fixing your
identity, file an extended fraud alert.
The purpose of an extended fraud alert is to mitigate the chances that your identity will become comp-
rised again in the future. Once this alert is in place, credit can’t be granted in your name until the creditor
contacts you directly via a method that you have specified (such as by telephone or email).
In order to file an extended fraud alert, you need to submit the following items to the credit bureaus:
- your identity theft report, which confirms your status as a victim of identity theft
- proof of your identity (each bureau will have its own requirements)
An extended fraud alert lasts for seven years, and identity theft victims are eligible for two free credit reports in
a twelve-month period. If you want to remove an extended fraud alert prior to the seven-year end date, you will
need to mail in the requests to remove them.

A credit freeze, also known as a security freeze, restricts
access to anyone trying to run your credit. However, pre-
existing creditors and debt collectors, as well as government
agencies with a warrant or subpoena, can still access your
credit account. This kind of freeze will prevent any new
creditors from obtaining any of your information.
A credit freeze can help prevent an identity thief who has obtained your information from opening
any new accounts with it. Most creditors will deny any attempt to open a new account if they are
unable to access credit reports.
Credit freeze laws differ from state to state. The cost for adding, temporarily lifting, and removing
credit freezes varies as well. Refer to this National Conference of State Legislators chart for the
detailed information you need based on where you live.
The cost for filing a credit freeze varies, but typically runs
around $10, though in most states credit freezes are free
foridentity theft victims. Keep in mind that you will need to
place the credit freeze with each of the three credit
bureaus individually and may have to pay a separate
fee for each.
Only YOU can request that a security freeze be filed
with each bureau, and only YOU can request that it
be lifted temporarily or removed.

If you do decide to place a credit freeze on your credit file, make sure to plan ahead for all your
credit applications. It can take up to three business days to lift a freeze once one has been
processed.
The best way to place a credit freeze is to submit a separate one online to each bureau.

Here are links to the freeze application for each credit bureau:
- Transunion(888-909-8872)
- Equifax (800-685-1111)
- Experian (888-397-3742)
If you are submitting your credit freeze by mail,be sure to include the following information:
- complete name (including any suffix, such as Jr. or Sr.)
- home address and proof of residence (such as a current phone or electricity bill)
- social security number and date of birth
copy of a government-issued ID (such as a driver’s license or passport)
If you want to lift your credit freeze temporarily, you will need to:
- submit the information detailed above
- include the 10-digit PIN that you will receive when you place your freeze
- specify the time period for the freeze (for example, June 1st-June 21st)
To remove your credit freeze permanently:
- submit the information detailed above
- include the 10-digit PIN
- provide two forms of identification (such as a pay stub with your address and a current phone
bill)
What a credit freeze or fraud alert doesn’t do
Credit freezes and fraud alerts are effective only when a transaction involves pulling your credit. So even though fraud alerts and credit freezes can help stop an identity thief from opening new accounts on your behalf, they can’t stop the threat posed by other forms of identity theft. Here are a few examples of situations not covered by credit freezes and fraud alerts:
- medical identity theft
- criminal record identity theft
- creditors who open accounts without running a credit check
- new bank accounts or health insurance accounts
- theft of an existing credit card or other account

Credit help for US service personnel: the active duty alert
When a member of the US armed forces is deployed, he or she can place an active duty alert in order to lower the chances of identity theft.
This kind of alert compels businesses to take extra measures before extending credit in the name of service personnel. An active duty alert lasts for one year and can be renewed to match the period of deployment. Once an alert is filed, the three bureaus remove the name from prescreened credit card offers for two years.

How to request an active duty alert
- Contact each credit report company and request an active duty alert.
- Provide proof of your identity with a government-issued identity card (such as a driver’s license or passport)
- Put a reminder on your calendar—since an alert lasts only one year, it is necessary to renew it for longer deployments.
- Keep notes of any calls and copies of any letters.

Specific Types
of
Identity Theft


Medical identity theft occurs when fraudsters use your information to obtain services from doctors, pharmacies, hospitals, or other treatment centers. If you believe that someone has used your information to receive medical treatment, immediately request a copy of your own medical records.
- Contact each hospital, pharmacy, clinic, and doctor with whom a thief may have used your
information and let them know the situation. - Request records from each provider (this may involve some fees).
- Check the health privacy laws for the state in which you live, since each state has its own
procedures regarding how to obtain medical records. - Federal law gives you the right to see your medical files. If any provider refuses to give you copies
of your own records, you have the right to appeal. If a provider still refuses to give you your medical
records within 30 days of written notice, you can file a complaint with the US Department of Health
and Human Services Office for Civil Rights at Health and Human Services by calling 866-627-7748 or
by going to this link.
Once you receive your medical records, go through them carefully and report any errors or unauthorized charges to every health care provider affected.
![]() Write a letter to each health care provider detailing the fraudulent medical treatment.
Write a letter to each health care provider detailing the fraudulent medical treatment.
![]() Include a copy of your medical report highlighting the disputed charges.
Include a copy of your medical report highlighting the disputed charges.
![]() Explain the circumstances of the fraud and ask the provider to correct it.
Explain the circumstances of the fraud and ask the provider to correct it.
![]() Include a copy of your identity theft report.
Include a copy of your identity theft report.
![]() Send each letter from your local post office by certified mail and obtain a return receipt.
Send each letter from your local post office by certified mail and obtain a return receipt.
![]() Notify your health insurer about the fraud.
Notify your health insurer about the fraud.
![]() Send your identity theft report to your insurer’s fraud department.
Send your identity theft report to your insurer’s fraud department.
![]() Check your credit report for any medical billings that have been flagged for non-payment.
Check your credit report for any medical billings that have been flagged for non-payment.
![]() Contact each credit bureau, following the directions listed above, regarding the fraud.
Contact each credit bureau, following the directions listed above, regarding the fraud.
![]() Keep detailed notes of every conversation, including whom you spoke with and the date and time. Keep copies of every letter that you send out. Each health care provider has 30 days to respond.
Keep detailed notes of every conversation, including whom you spoke with and the date and time. Keep copies of every letter that you send out. Each health care provider has 30 days to respond.
Here are some pieces of information that can help convince providers that you yourself were not the recipient of the disputed services:
- The physical description of the patient: all intake charts include such identifying characteristics as
height, weight, ethnicity, age, and sex that can be used to show that you are not the one who
was treated in your name. - The date services were conducted: it may be possible to prove that you were elsewhere at the
time when the fraudulent care was provided. - The type of service that was given: in such cases as surgery or a diagnosis, you may be able to
prove that the care was delivered fraudulently by not having a surgical scar or the condition that
was diagnosed.

Tax Identity theft is an increasingly common problem that is in part due to the slow and inefficient system used by the Internal Revenue Service (IRS), which identity thieves are able to exploit. The IRS is, however, aware of the problem and taking steps to combat it.
If you receive an notice from the IRS that your social security number was used fraudulently to get a tax refund, carefully follow the instructions that accompany the letter.
- Mail in or fax Form 14039, the IRS Identity Theft Affidavit, to the IRS along with your identity theft
report. - Include proof of identity, such as a photocopy of your driver’s license or passport.
- After mailing or faxing these documents, call the IRS at 800-908-4490 and keep detailed notes of
the date and time of your call and whom you spoke with. - Request an IP PIN (The Identity Protection PIN). Once you notify the agency that you are a victim
of identity theft, the IRS will issue you an IP PIN, which is a 6-digit number that you will use when filing
your tax return. Don’t give this PIN to anyone, apart from a tax preparer if you use one. Once you
receive your IP PIN, you must use it when submitting your FEDERAL taxes, or they will be rejected
(note that you don’t use your IP PIN for your state tax filing). One more important point: once you
have been issued an IP PIN, you can’t opt out; you must file e-file with your IP PIN or your tax filing
will be rejected, leading to substantial delays in processing. - As always after any kind of identity theft, place a fraud alert with the three credit bureaus to
protect yourself from future damage (see above for the contact information).

Surprisingly, the theft of children’s identities is the fast-growing kind of identity theft. Children are naturally unlikely to know that they have been victims until they grow older and apply for their first credit cards or car loans. By then, the identity thief will be long gone, leaving a wake of credit destruction.
If someone uses your child’s information to commit fraud, start by contacting the company where the fraud took place.
- Provide as full an explanation as possible regarding how your child became a victim of identity
theft and as many details as you can about the fraudulent account in the child’s name. Make
sure that the company understands that your child is still a minor and therefore cannot legally
enter into a contract. - Demand that the fraudulent account be closed and that a letter be sent confirming that your
child is not liable for the account. - Send the company a letter including the Minor’s Status Declaration and include a copy of your
child’s birth certificate. - Keep detailed notes of whom you contacted and the date and time.
If you suspect that your child’s identity has been compromised in ways that have yet to be discovered, request a manual search for his or her social security number from the credit bureaus, each of which has its own process.
Remember that children normally don’t have a credit history unless an identity thief has used their information. If a credit report is generated for your child, a copy will be sent to you. Follow the instructions provided to remove the fraudulent accounts from their record.
To make sure that your child’s identity remains inaccessible to thieves, place a credit freeze on his or her social security number, which in most states is free for minors. Click on the following links and follow the directions of each credit bureau:
- Experian
- TransUnion – Request must be submitting in writing: TransUnion Protected Consumer Freeze?P.O.
Box 380?Woodlyn, PA 19094 - Equifax – Request must be submitted in writing: Equifax Security Freeze, P.O. Box 105788, Atlanta,
Georgia 30348

If you suspect that fraud being done in your name involves your driver’s license, call your department of motor vehicles to see if another license has been issued in your name, and then follow these steps:
- Place a fraud alert within your DMV records.
- Go to your local DMV office and ask for a new driver’s license number.
- Fill out a DMV complaint form to start the fraud investigation process.
- Bring any supporting documentation that will help your case.


What to do if your
information is exposed
in a data breach

According to a Javelin Strategy & Research study, nearly one in three data individuals whose information is compromised in a data breach becomes a fraud victim within the next twelve months. Federal law states that companies must inform their customers of any breach of confidential information. If you are unfortunate enough to have dealings with a company that experiences a data breach, you should receive a letter or email explaining exactly what information was exposed and when.
If have been a victim of a data breach resulting in fraud in your name, immediately go to this link at identitytheft.gov and report the issue (click on “get started” and scroll down to “my information was exposed in a data breach”).
what you should do to protect yourself:
Credit card: Call the credit card company and ask for a new card with a new number.
Thanks to the Fair Credit Billing Act, you will NOT be liable for any unauthorized
purchases following a data breach.
Debit card: Call your bank and request a new card and number, and be sure to
change your PIN as well. If your card was not lost, you are not liable for any
unauthorized purchases, provided that you report them within 60 days of receiving
your statement.
Bank account: If your bank account has been exposed in a data breach, close it
and open a new account. Ask the bank to create a verbal password for your
account, which prevents the release of any information without password verification.
Email address: In general, be vigilant about changing your email password regularly.
Keep an eye on any suspicious messages in your inbox requesting information or
asking you to click on a link. If you receive an email from a company with which you
do business, call the number on their official website to verify that they sent you the
email.
Social security number: If your SSN is exposed in a breach, immediately contact the
three credit bureaus and place a fraud alert, as discussed above.
A special note about the IRS: There have been a
few major breaches of IRS data in recent years.
If you become a victim of such a breach, make
sure to request an IRS pin forprotection from
fraudulent tax returns being filed in your name.
Increase your awareness of data breaches by
customizing your Google News feed (for instructions,
watch this 90 second video). Since these breaches
occur frequently, consider having Google notify
you when a new one occurs. You can enter such
specific keywords as “data breach” so that Google
will show you articles related to your search and
you will receive up-to-date information of any new
data breaches.
Here’s a screenshot of how to input keywords:
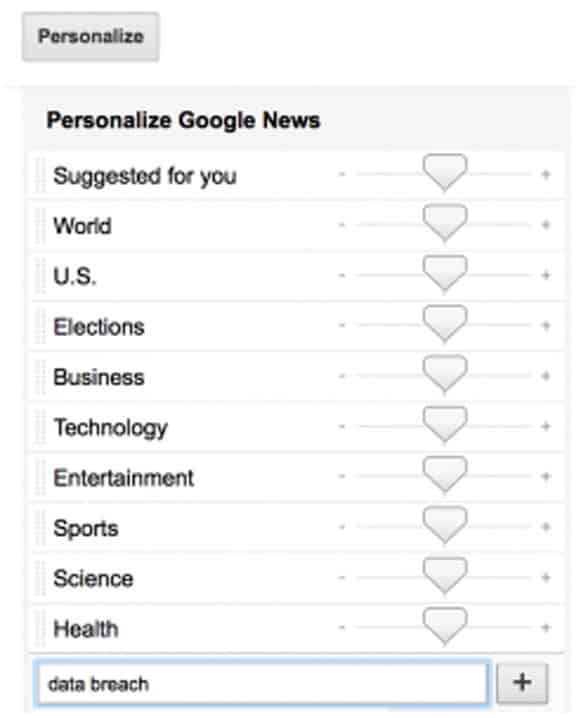
Since data breaches are becoming increasingly common, some of the larger
companies have begun offering free credit report monitoring. This service can be a
real benefit, since companies are usually able to notify you when a case of fraud
occurs long before you would be able to find out about it.

Cyber thieves have learned how to use the phone to hack into your computer. They may call you and claim to be from a well-known company, such as Geeksquad or Microsoft.
A common scam is to claim that a virus has been found on your computer and that you need to grant them remote access or to buy software to clean up your computer. The purpose of this scheme of course is not to protect you from viruses, but to take your money. These thieves create fake websites that offer a “ free security scan ,” and they often send ominous messages to convince you that your computer has been infected. Then they sell you bogus software to fix the non-existent problem. To make matters worse, some of these fraudsters send malicious software, known as “malware,” that gives them access to your computer and personal information.
So, if someone calls you claiming to be a technical support representative, hang up immediately. Here are some tips for avoiding tech support scams:
![]() Any caller who claims that an emergency has occurred or uses other high pressure tactics is probably a scammer.
Any caller who claims that an emergency has occurred or uses other high pressure tactics is probably a scammer.
![]() Never provide any credit information to a caller; no legitimate company will ask for your credit card number, expiration date, or security code over the phone.
Never provide any credit information to a caller; no legitimate company will ask for your credit card number, expiration date, or security code over the phone.
![]() Never give any customer service representative your online passwords.
Never give any customer service representative your online passwords.
![]() Never grant a caller remote access to your computer.
Never grant a caller remote access to your computer.
![]() Don’t rely on caller ID; cyber criminals have sophisticated technology that can cloak where their true identities.
Don’t rely on caller ID; cyber criminals have sophisticated technology that can cloak where their true identities.
If you do receive a suspicious tech support call, be sure to place your phone number in the National Do Not Call Registry, and then report the call to the FTC.
Actions that may be appropriate, depending on your specific case.
![]() If you suspect that your social security number has been used illegally, contact the Social Security Administration fraud hotline at 800-269-0721. You can apply online to get a new card for free.
If you suspect that your social security number has been used illegally, contact the Social Security Administration fraud hotline at 800-269-0721. You can apply online to get a new card for free.
![]() In order to prevent debt collectors from attempting to collect debts that you don’t owe, contact the debt collector in writing by mail within 30 days of receiving notice about the fraudulent charges. This sample letter can serve as a template.
In order to prevent debt collectors from attempting to collect debts that you don’t owe, contact the debt collector in writing by mail within 30 days of receiving notice about the fraudulent charges. This sample letter can serve as a template.
![]() If you suspect your mail has been stolen or misdirected, contact the US Postal Service at 800-275-8777 to obtain the number of your local US Postal Inspector. You may wish to rent a P.O. Box at your local post office to prevent your mail from being stolen.
If you suspect your mail has been stolen or misdirected, contact the US Postal Service at 800-275-8777 to obtain the number of your local US Postal Inspector. You may wish to rent a P.O. Box at your local post office to prevent your mail from being stolen.
![]() If your passport is stolen, contact the US Department of State at via this link or call 877-487-2778. They can also help if your passport has been stolen or lost while you are in a foreign country.
If your passport is stolen, contact the US Department of State at via this link or call 877-487-2778. They can also help if your passport has been stolen or lost while you are in a foreign country.
![]() For stolen checks, first contact your bank, and then call Telecheck at 800-366-2425 in order to place a fraud alert on your account so that unauthorized checks will be refused.
For stolen checks, first contact your bank, and then call Telecheck at 800-366-2425 in order to place a fraud alert on your account so that unauthorized checks will be refused.
![]() Always take detailed notes when you discuss your case with anyone, including name, date, contact information, and the subject of the conversation. Make and keep copies of all documents, emails, reports, and letters that pertain to your case.
Always take detailed notes when you discuss your case with anyone, including name, date, contact information, and the subject of the conversation. Make and keep copies of all documents, emails, reports, and letters that pertain to your case.
![]() Change all passwords and pin numbers for every account you have.
Change all passwords and pin numbers for every account you have.
If you suspect that your identity has been compromised, immediately follow the steps provided in this article. The sooner you take action, the sooner you will be able to secure your identity again.

Ways to
Prevent
Identity Theft

Of course, the best way to deal with identity theft is to be proactive and limit your
exposure to fraud. Here are a set of simple steps that you can take to prevent i
dentity theft in the future.
Don’t disclose your personal
information online.
Social media allows you to connect with friends and loved ones as well as business contacts. But
you may be surprised to find out who is actually looking at your account. Never assume that your
personal information is private when you make it available on social media sites. Hackers can use
these sites to access your data, so don’t put any information on the web that can help an identity
thief to create or verify cash, credit, or service transactions.
Purchase an anti-virus program
There are many ransomware and malware scams out there that pose a potential threat to your computer. Make sure to buy a well-known and established anti-virus program to protect your computer. These programs continually scan your computer for suspicious files and block malware from doing damage.
Limit your use of public Wi-Fi
Open and public networks are easier to hack into than your private service at home or work. In particular, never use a public network to access online banking or to pay any type of bill. Cyber criminals may be waiting for you to use your mobile phone or laptop while you are at a coffee shop and steal your login info for your private accounts.
Buy a shredder and use it
Every member of your household should get in the habit of shredding anything with personal information on it. Shredders are cheap and well worth the price to keep dumpster divers from stealing your information from the trash. There are statistics that show as much as 88% of stolen identifying information comes from criminals going through trash.
What to shred:
- old utility bills
- junk mail
- bank/investment/credit card statements
- anything with your name and an account number on it
- pay stubs
- membership information
- any type of contract, including ones that have already been completed
Get a P.O. box at your local
post office
Stealing mail is still one of the most common ways that thieves obtain personal information. A P.O. box is secure against this kind of theft. Using a P.O. box may be inconvenient, and it costs a little, but considering the personal information that can end up in your mailbox, it’s definitely worth it.
Password Security
Security experts highly recommend using a different password for every account. This means keeping track of multiple passwords, but it’s definitely worth the hassle given the amount of damage that hacker could do with access to all of your accounts. Take the proper precautions and make sure that you don’t allow easy access to your accounts because you want the convenience of using the same password for everything. For help creating secure passwords, you may want to try using a password generator, such as such as this one by Norton.
Here are some tips for creating a solid password:
- Use at least seven characters.
- Use a combination of upper and lower case letters, numbers, and special characters.
- Never use personal names or the word “password.”
use 2 step verification whenever possible
Most people only have one layer to protect their account. With 2-step Verifications, i an identity thie hacks your password, they’ll still need your phone or Security Key to get into your account.
Don’t worry, you can choose not to have 2-step verificaion on your home computer. But if you or someone else tries to sign in to your account from another computer, 2-step veriication will be required.

Avoid using non-bank ATMs

Fraud using ATM skimming devices are on the rise. FICO reported a 6-fold increase in the amount of
ATMs in the US compromised by criminals from 2014 to 2015. In the words of T.J. Horan, vice
president for fraud at FICO, “60% of compromises were at nonbank ATMs. If you have an opportunity
to go to a bank ATM instead a generic one, do it.”
Watch out for shoulder surfers
“Shoulder surfing” is when criminals sneak looks at your computer or at an ATM that you are using in order to get steal your PINs, security codes, or passwords.
Tips to prevent shoulder surfing:
- Be aware of your surroundings before entering your PIN at any ATM.
- Make sure your transaction is completed before walking away from an ATM.
- Try sit in a place where someone else can’t see the screen when you are using your computer in a public place.
- Keep an eye on the mirror at the ATM to make sure that no one is looking over your shoulder,
and don’t hesitate to ask someone to back up a bit.
Be careful when making online purchases
If you have never done business with a particular vendor online, make sure to verify that the vendor is trustworthy by going to the WOT (Web of Trust).
Follow these steps to avoid disclosing financial details to identity thieves:
- Shop only on well known and trusted sites.
- Use a separate credit or debit card for online shopping; this makes it easier to track your purchases and allows
you to pinpoint any transaction that doesn’t look familiar. - Make sure that the web address of any business with which you do online business starts with “https” (rather than
“http”). The extra “s” indicates that the site has an SSL certificate (secure socket layer), meaning that it is verified
as being secure by web hosting companies. - Paypal is a great alternative to using a credit card. When you use Paypal, the seller never has access to your
credit information, and you are covered by Paypal’s guarantees.

Don’t open
emails from
people you
don’t know
If you get an email from an unknown sender that includes attachments, DO NOT open them, since this is an easy way for cyber criminals to track your “metadata,” which can in turn reveal your private information. Malicious attachments can also include a “ Trojan horse” program for breaking into your computer.
Be on the watch for “phishing” scams
Phishing scams, which were mentioned above, have been around since the advent of the internet. These scams use emails disguised as legitimate business communications, and are designed to lure unsuspecting people into disclosing their personal information, which can then be used to perpetrate fraud.
Don’t trust emails from anyone claiming to represent a company with which you conduct business that ask for personal information. Go to the company’s home website and call their official number in order to whether the email actually was sent by the company.
Also, be sure to forward phishing emails to spam@uce.gov and to the company or organization impersonated in the email in order to help bring these scammers to justice.

Stop receiving junk mail and telemarketing

Go to the DMA Web Form to stop junk mail from clogging your mailbox and giving identity thieves
information that can be used to defraud you. The most direct way to do this is to call 888-567-8688,
which is the opt-out line for all three credit bureaus; here are the relevant links for
Experian, Transamerica (scroll down to “opt out”), and Equifax. The 888
number accesses an automated voice response system through which
you can opt out of all credit related offers for two years, or permanently
if you prefer, though this requires filling out and submitting a form.
Here is a list of the top data brokers in the country, which make their money by selling
your information to businesses and organizations. To put a stop to unwanted solicitation,
write to each of them individually and demand that your name be removed from all their
telemarketing lists, which they are required to do, though the block will take a few months to
go into effect.

Metromail Corporation

List Maintenance
901 West Bond
Lincoln, NE 68521
R.L. Polk & Co. –
Name Deletion File

List Compilation Development
26955 Northwestern Hwy
Southfield, MI 48034-4716
What to do when telemarketers call
All you need to say to a telemarketer is, “Please put me on your do-not-call-list.” That’s it.
Keep a careful eye on your bank and credit card statements
To ensure that your accounts don’t register any unauthorized charges, take a few minutes going over your
statements as soon as they arrive. Better yet, log on to your
online accounts on a weekly basis rather than waiting until your monthly statement cycle comes through.
Purchase identity theft insurance
There is only so much that you can do to minimize your chances of identity theft. Even if you follow every tip in
this guide and lock up all your personal info, the possibility remains that a hacker will somehow gain access
to your information.
One powerful way to mitigate the potential damage of credit fraud and to enjoy peace of mind is
by engaging an identity theft protection company. If you do then happen to fall victim, these companies will do the heavy lifting on your behalf to restore your credit rating and take care of fraudulent charges.
Get your free credit report
Every US citizen or resident is entitled to one free credit report per year. Just go to annualcreditreport.com
and get your personal report from all three credit bureaus for free. By viewing your credit reports, you
can determine whether anyone other than yourself or someone that you have authorized is using your identity.
It is a good idea to order credit reports quarterly so that you can monitor your credit profile throughout
the year. Some identity theft protection companies include credit reports along with monitoring services.

Keep your computer and
software up to date

Keep your eyes open for the latest updates and install them when they become available
so that you can patch any holes that have been detected by security experts.

Secure your smartphone
People take their phones wherever they go,
and a smartphone contains a lot of personal information
of the kind that identity thieves would love to access.
Here are a few steps to follow to help keep the data
from your smartphone from ending up in the wrong hands.
- Always know the whereabouts of your
phone, and instruct your children about
the potential danger if their phones are
lost or stolen. - Use strong passwords to access your phone,
or even better use a phone with fingerprint
authentication - Only download apps from companies that 4
you know and trust. - Download an app for GPS that incorporates
a remote wipeout mechanism.